Depreciated Walkthrough Proving Grounds
I went ahead and grabbed the IP address of the target machine and ran two nmap scans, the first one scanning all ports to see what was open, and then the second was a script and version scan to enumerate the services running on the open ports.
I noticed that port 5132 was running a python script in “/opt/depreciated/messaging/messages.py”. I thought this was very interesting. I decided to check out port 80 to see if there was any information on the web server that was running.
Port 80 told me that the Web UI is down but the CLI app on port 5132 is up which is running that python script. I decided to check out the source code too.
The source code told me that in order to login to the web UI, it used graphql on port 8433. So I copied that address and pasted into the browser changing the IP from home to public IP.
It shows the API information in JSON format. After googling “GraphiQL exploit” I found this page: http://book.hacktricks.xyz/network-services-pentesting/pentesting-web/graphql. It gave me some query’s to try such as this:
Using the following URL syntax I was able to get some information.
http://192.168.152.170:8433/graphql?query={__schema{types{name,fields{name}}}}
So now I can see that I can list users and get “OTP” which is one time password.
So I try to list the users first using this URL syntax: http://192.168.152.170:8433/graphql?query={listUsers}
Awesome! It gave me two usernames, peter and jason! now lets see if we can get a OTP using the following URL syntax: http://192.168.152.170:8433/graphql?query={getOTP}
Unfortunately, it won’t just give me a OTP, the error message says it’s missing an argument for “username” and that it needs to be a string. So using this information, I was able to provide a username for the OTP using this URL syntax:
http://192.168.152.170:8433/graphql?query={getOTP(username: "peter")}
Success! I now have a username and OTP! Let me try and get one for the other user as well.
Now that I have two usernames and OTP, I’m going to try and login to the CLI since I can’t login to the web UI as the page is under maintenance. I tried logging in with Jason, but would not let me login, so I logged in with Peter.
I remembered that this is a python script running a messaging service. I typed help to get a list of commands. These are my options. I decide to list the messages and try reading them.
I wasn’t able to read all but one of the messages, which is telling me to change the password for Peter. It looks like it lists the password for Peter! I also tried to read #0 as well, which looks like its starting off saying something about a password issue, but it wouldn’t let me read it.
I try to SSH in as peter with the password peter@safe
Success! I grabbed the local.txt file and then downloaded linPEAS onto the target machine using python server on port 80.
I didn’t really find anything with linpeas. Possible kernel exploits, but I wanted to avoid doing those as I generally avoid them for stability purposes. I went back through and realized we still had that python script that was running on port 5132 and it was in the opt folder.
Taking a deeper look into this folder, I find the app “messages.py” which is owned by root but I have reading permissions for it, so I look at it.
In short, this code defines a function for creating messages in a messaging system, including optional file attachments. It stores these messages in memory and also saves them to a JSON file for later retrieval located in “msg.jason”. Unfortuneatly msg.json is only readable by root.
With this information I’m wondering if that message #0 I saw earlier contains information to priv esc. That message should be stored in msg.jsaon according to how this script operates.
Something else I noticed about about the script is that it allows attachements. Since this application is owned and run by root, it opens whatever attachment is listed, and then writes that to /opt/depreciated. So my thought process is to login as peter on port 5132, create an attachment and use the msg.json as the attachment. Root user will open, read, and then write msg.json to /opt/depreciated/msg.json, which peter should have reading rights to.
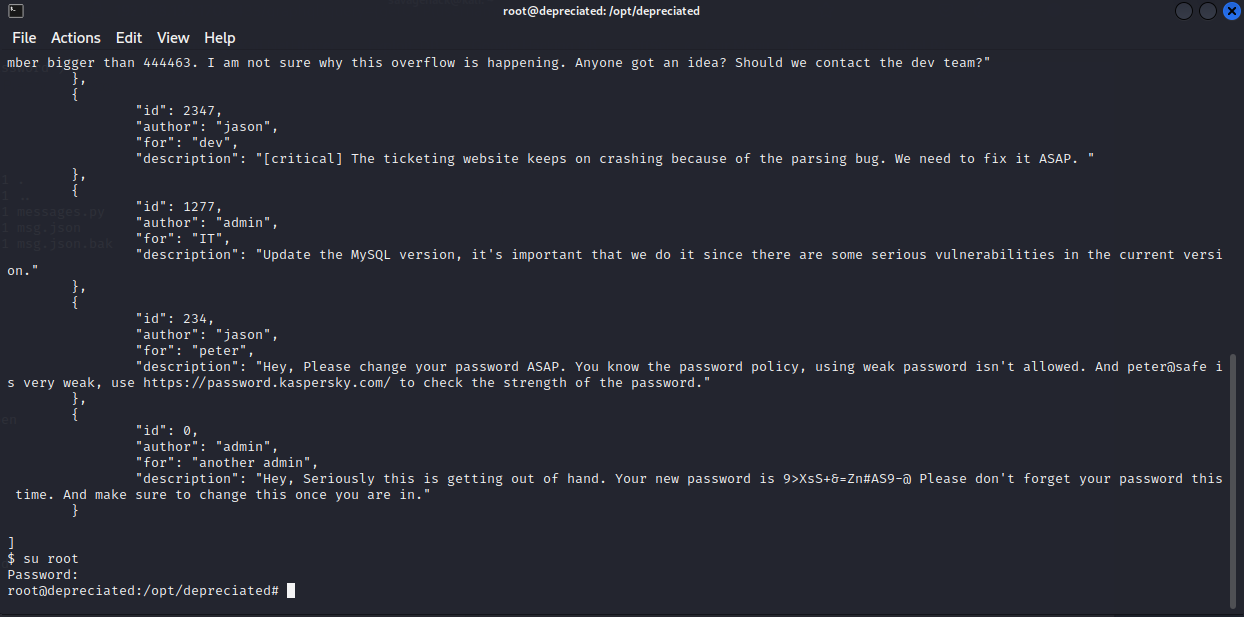
It worked! I’m able to see all of the messages now.
I see the message #0 and its from an admin to another admin and lists a password. I try to su to root using this password.
And I have root!
-Sam